Penetration Testing from the Experts
Whether you need to meet regulations, demonstrate compliance or you simply want to know where the vulnerabilities are within your business, a penetration test will help identify how secure your technology, processes, procedures and people really are.
All businesses can benefit from undertaking a penetration test, because the first step in protecting your business from today’s constantly evolving threat landscape is knowing where your vulnerabilities are so you can address them.
A penetration test is an absolute essential, where businesses:
Have applications that are client facing
Have a team of app developers
Are subject to regulations like DORA; MFID; PCI-DSS; KCSiE; NIS2; Cyber Essentials and many more
Are third-party supplier to a business / organisation that is subject to regulation
Are looking to purchase Cyber Insurance
What is a Penetration Test?
A penetration test is a point in time assessment of a company’s external, internal and public facing infrastructure. Its aim is to identify and confirm vulnerabilities, to allow organisations to remediate any risks and weaknesses discovered.
How does the Koris365 Penetration Test work?
We test all of the software and technical infrastructure that keeps your business systems up and running. Identifying vulnerabilities that may exist, for example; in authentication; cross-site scripting; source code; logic; and insecure network configurations.
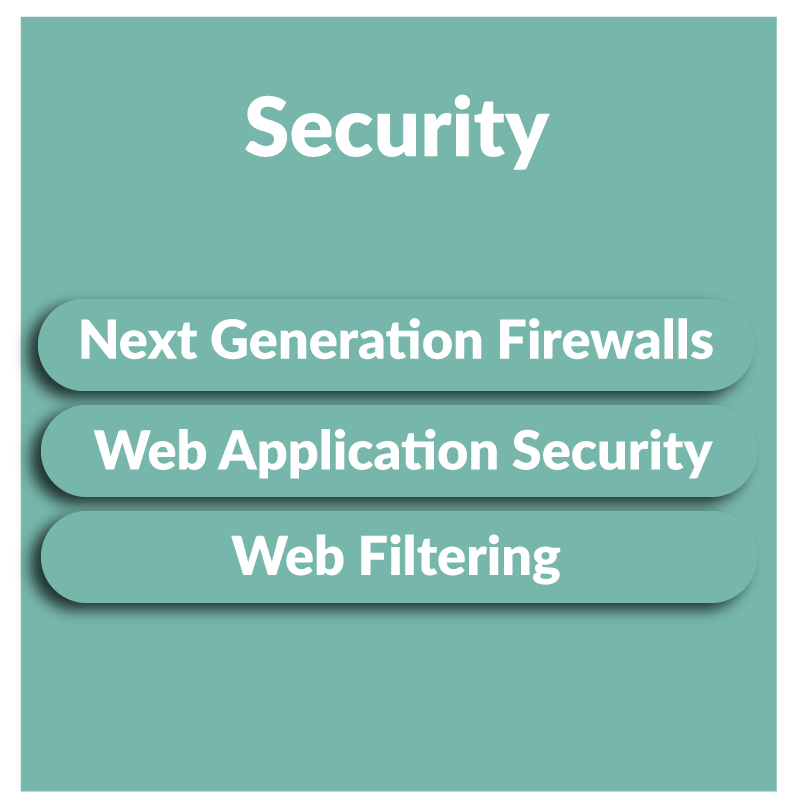
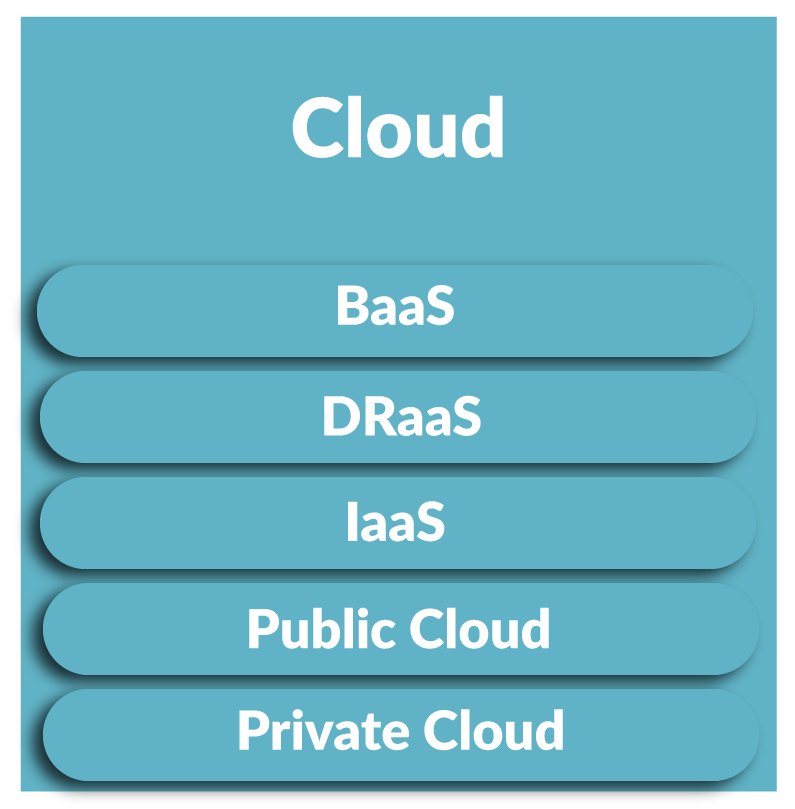
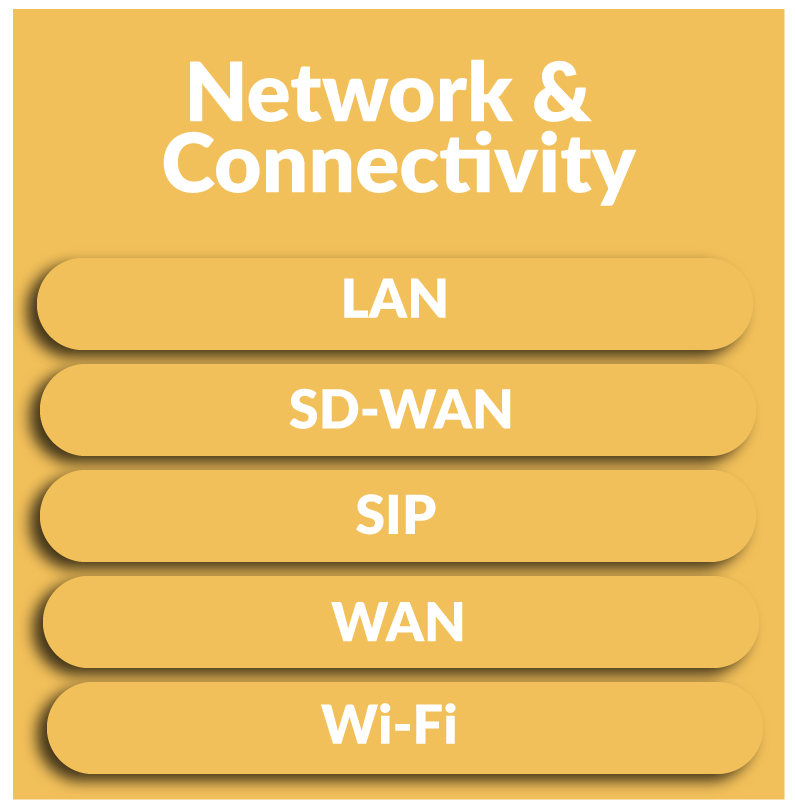
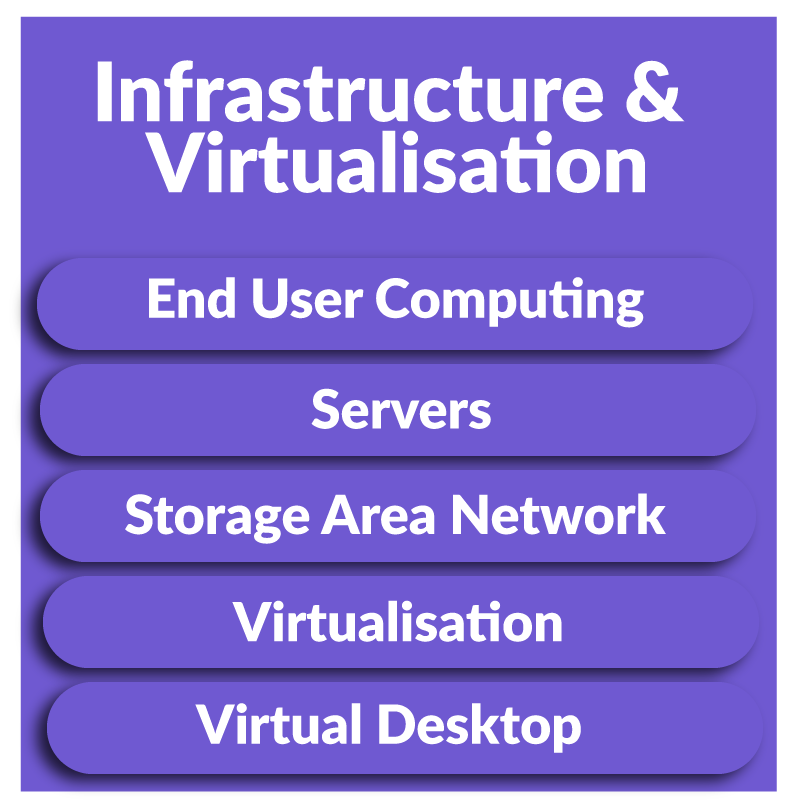
Our testing can cover external facing infrastructure, such as websites, login portals, applications and cloud services, and or, your internal infrastructure looking for vulnerabilities and weaknesses in your servers, switches, routers and end points.
The experienced team of CREST and CHECK certified testers use a variety of commercially based tooling, alongside their own bespoke tools and techniques to provide a comprehensive report on what is both secure and what needs improving.
Penetration Tests
Identify and eliminate technical vulnerabilities
Improve your application’s security posture
Safeguard your critical infrastructure
Ensure your risks are covered across all assets
Protect your cloud environments
Meet regulatory compliance
Our other Cyber Security Services include:
.1
Microsoft 365 Assessments
.2
Maturity & Gap Analysis Assessments
.3
Policy and Process Assessments
.4
Cyber Assessment Framework
.5
Technical Assessment
.6
Ransomware Attack Simulation Service
.7
Cyber Essentials Certification
.8
Red Teaming, Blue Teaming and Purple Teaming
For more information on other Cyber services such as SOC, SIEM, Cyber Assessments, Microsoft 365 Cyber Assessments please contact us.
Contact us
We would love to hear from you. To get in touch with our team of technical experts, please fill out this form or contact us by phone or email