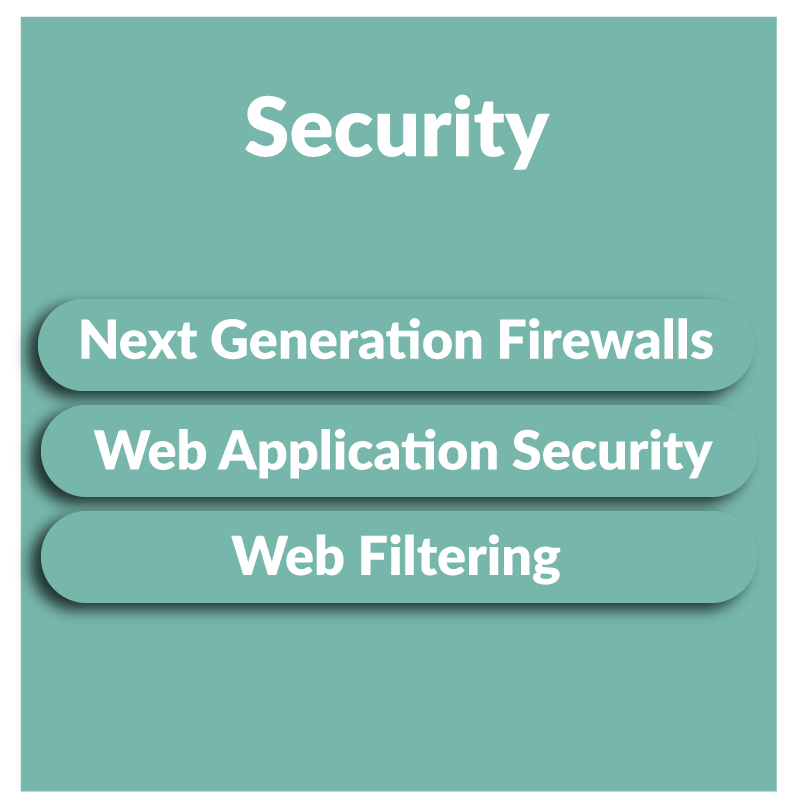
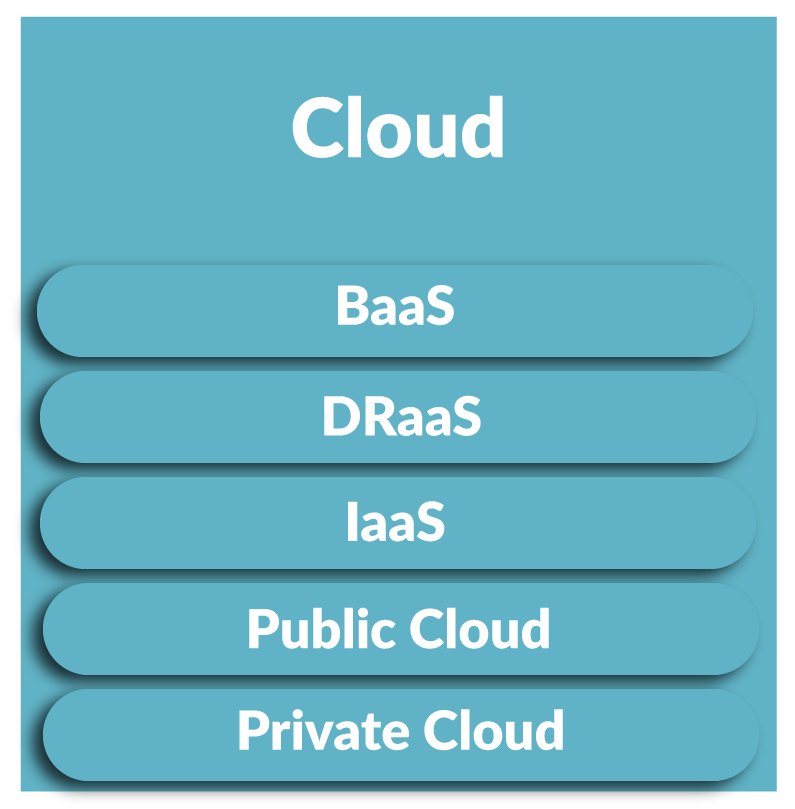
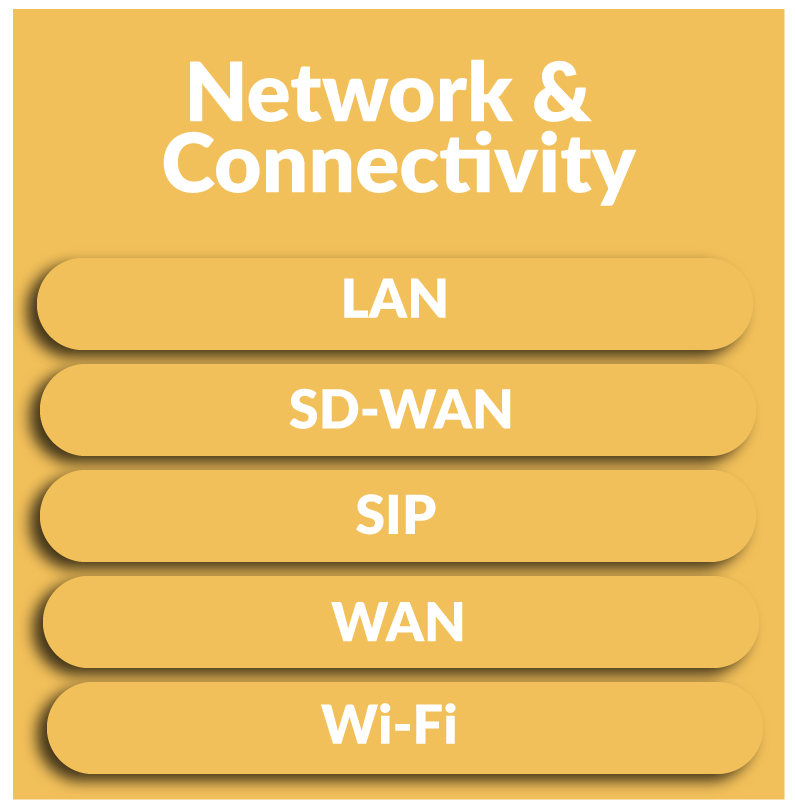
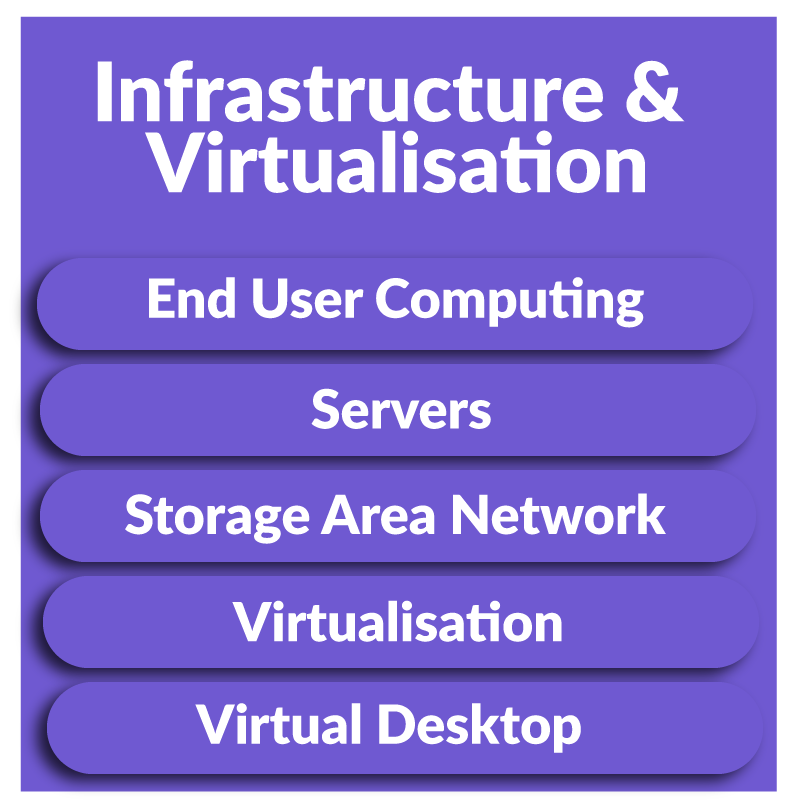
Red Team Testing Services & More
Delivered by highly trained and experienced experts
Simulating real world adversaries
If you’d like to really test your business’s security profile, look no further than Red Team & Attack Readiness Services. Simulating real-world attacks to understand how well your business systems and people will defend and respond will provide extensive insights and intelligence you can use to increase your security profile maturity.
Delivered by highly trained and experienced experts, all of whom have a deep knowledge of the tactics, techniques and procedures being used against businesses today: these services provide a detailed insight into the vulnerabilities within your business.
Insights; Intelligence inspiring changes to improve robustness
Security Testing Maturity
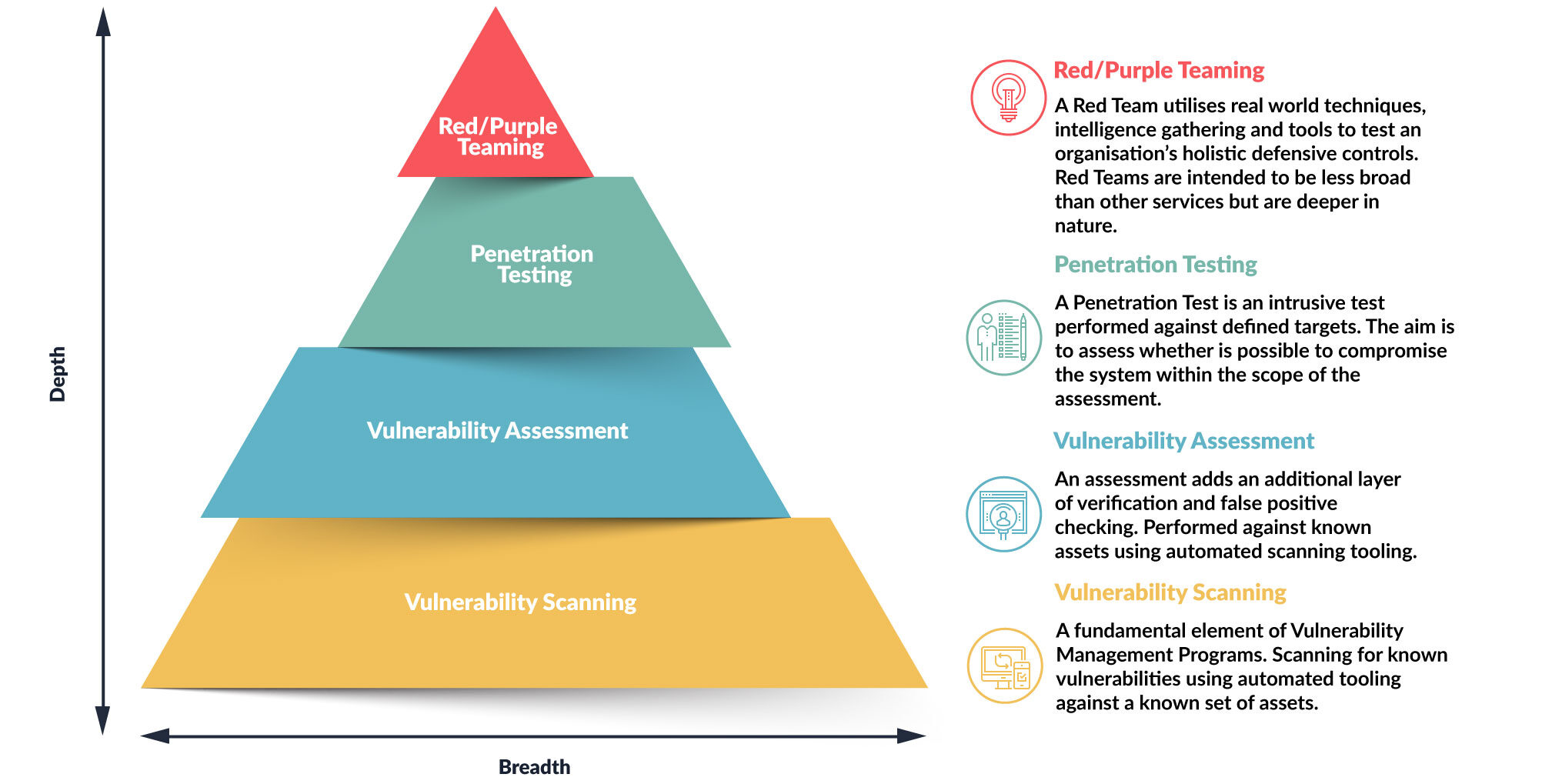
Red Teaming & Attack Readiness Services
Used to understand your susceptibility to attack and ability to detect and respond.
Our services can be delivered in a few different ways:
Red Team Engagement (Simulation of a real-world attack)
This involves simulating an actual attack on an organisation to evaluate its security defences. The Red Team (offensive) tries to compromise systems, bypass security, and identify weaknesses, while the Blue Team (defensive) works to detect and respond. This exercise focuses on identifying real vulnerabilities whilst remaining covert. Objectives and clearly defined scenarios can be defined to ensure meaningful outcomes.
Purple Team Engagement (Watch and learn from systems’ responses to simulated attacks)
This type of engagement involves collaboration between the Red Team (attackers) and Blue Team (defenders). Both teams work together to improve the organisation’s detection, response, and prevention capabilities. The Blue Team watches and learns from the simulated attacks, using them to refine their defences
Cyber Readiness Assessments (Independent assessments)
These are evaluations performed by us to determine how prepared an organisation is for a cyber attack. It involves assessing policies, procedures, security controls, and the ability of the organisation to detect, respond to, and recover from cyber incidents.
Tabletop Dry-run Assessments (Working with your team to understand)
A tabletop exercise is a discussion-based session where team members walk through the steps of responding to a simulated security incident or breach. This helps the team understand their roles, responsibilities, and the effectiveness of the incident response plan without the pressure of a real attack.
All things Cyber Security
Our team of Cyber Security experts have much to share. Therefore, be sure to check back regularly.
Contact us
We would love to hear from you. To get in touch with our team of technical experts, please fill out this form or contact us by phone or email